 In the Spring of this year, I used baseball as a metaphor for the “game of Long Term Care.” At that time I said that providers were “going to have to step up to the plate and respond swiftly and powerfully to the curve balls of regulatory changes, the sliders of reimbursement, the change-ups of market pressures, and the fast balls of competition.” Little did I know at the time that the term, “sliders of reimbursement,” was going to be uncomfortably prophetic. Because of the drastic “adjustments” to Medicare reimbursement and declining Medicaid rates, the slider is real – a potential slide downhill, that is; they’re game changers. I would like to take the baseball metaphor one swing further.
In the Spring of this year, I used baseball as a metaphor for the “game of Long Term Care.” At that time I said that providers were “going to have to step up to the plate and respond swiftly and powerfully to the curve balls of regulatory changes, the sliders of reimbursement, the change-ups of market pressures, and the fast balls of competition.” Little did I know at the time that the term, “sliders of reimbursement,” was going to be uncomfortably prophetic. Because of the drastic “adjustments” to Medicare reimbursement and declining Medicaid rates, the slider is real – a potential slide downhill, that is; they’re game changers. I would like to take the baseball metaphor one swing further.
A successful swing at the plate requires not only skills, talent, great vision, quick reflexes, good upper body strength, and sound judgment, but a solid bat as well, one that each batter can handle comfortably and confidently. It’s the tool that hitters rely on. In the case of LTC, the “bat” I am referring to is IT (information technology). And it’s time for IT to prove its worth as a tool to identify savings without cutting quality and to prevent unnecessary revenue leakage through automated tools and processes.
Savings – the IT Infrastructure
Let’s start with IT itself. Article upon article and one study after another have clearly identified that the “cloud” offers the scalability, flexibility, reliability, and savings that other methods of IT deployment may not offer. Cloud-based computing means lower initial costs and TCO, because all IT-related procurement, maintenance, management, and upgrades are handled remotely. Further, the cloud’s monthly subscription-based model enables providers to use their capital for other critical areas of their business. Earlier this year, the CIO Consortium identified that, “Reasonable, five-year costs to deploy currently available EMR technology and eliminate paper records range from $254,000 per facility for third party hosted solution (italics and color added for emphasis), $259,000 for vendor hosted Software as a Service (SaaS), and $356,000 for an in-house hosted solution.” Clearly, now is the time to carefully consider the cloud as a solid source for immediate and long-term savings.
Real Savings through IT Tools
What specifically does IT offer that will help providers identify savings, stop revenue leakage, and ensure that they are in compliance with regulations? The answer is automation - automated claims management to stop revenue leakage; automated MDS and RUGs reporting; automated procurement to make sure that purchases are per contract pricing, timing, and quality; automated labor management; and automated real-time Key Performance Indicator (KPI) reporting.
Automated claims management helps providers not only to generate, review, edit, and transmit claims, but to identify and act immediately on issues when and where they occur. This includes incorrect claims codes, codes changes and regulations, missing codes, poor communication between clinical and billing staff, poor pricing practices, and inefficient and ineffectual internal review processes.
Automated MDS and RUGs reporting lets providers identify facilities most "at risk" with poor survey performance; discover how each of their facilities ranks among its peers; pinpoint facilities which are operating below or above critical primary care staffing levels; detect residents/patients who are clinically at risk; observe the financial impact of MDS submissions by facility, region, and corporation; scrutinize QM/QI’s at a facility, region, or corporate level, and analyze reimbursement rates (RUGs).
Automated procurement involves complete commerce automation (purchase orders, invoices, and product and contract maintenance) and reporting with intelligent direction and feedback for procurement decisions. It connects multiple facilities, satellite locations, and branch offices to the vendors, products, pricing, delivery terms, and service providers carefully negotiated and selected by their parent company. Automation allows flexibility and customization for each corporate entity to support their partner selection, the business rules negotiated with each partner, their internal G/L structure, and their purchasing chain of command.
Automated labor management gives providers the tools necessary to manage and control that which amounts to almost 60-70% of a provider’s spend – labor. Automation offers applicant tracking, time and attendance, payroll, and human resources management. Not only can providers reduce costs wisely, but also increase productivity.
Automated real-time Key Performance Indicator (KPI) reporting, or a digital dashboard, translates into business intelligence, which to LTC providers means they can quickly analyze and act on census levels, admissions, and discharges; labor hours and costs; and receivables and collections. Armed with this incredibly valuable information, providers are able to monitor how well they are saving money and increasing revenue in real time and take action, when necessary, with surgical precision.
Summary
IT through the cloud will not only help providers survive, but ultimately win, by confidently hitting whatever is thrown at them out of the park.
/Prime-Care-Technologies-Logo.png?width=191&height=55&name=Prime-Care-Technologies-Logo.png)

 What is the ROI? Last time, I highlighted some of the features of the fully-automated procurement process. As attractive as the various features sound, the real synergy occurs when Buyers experience real savings. In today’s sluggish economy, in general, and because of dramatically contracting reimbursements for health care providers, specifically, ROI must be real and attainable.
What is the ROI? Last time, I highlighted some of the features of the fully-automated procurement process. As attractive as the various features sound, the real synergy occurs when Buyers experience real savings. In today’s sluggish economy, in general, and because of dramatically contracting reimbursements for health care providers, specifically, ROI must be real and attainable.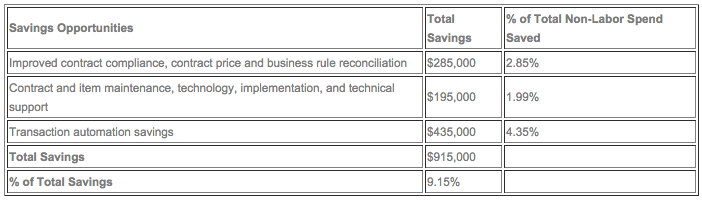
 In past blogs I’ve referred to Patronizing Partnership as the highest level of eProcurement Evolution, a Buyer/Vendor relationship marked by trust, cooperation, and mutual support. Let’s discuss this in more practical terms which go beyond the platitudes and attitudes, first by defining what is eProcurement Evolution, specifically, complete procurement automation. (In Part II, I’ll illustrate the benefits of eProcurement with a plausible ROI scenario.)
In past blogs I’ve referred to Patronizing Partnership as the highest level of eProcurement Evolution, a Buyer/Vendor relationship marked by trust, cooperation, and mutual support. Let’s discuss this in more practical terms which go beyond the platitudes and attitudes, first by defining what is eProcurement Evolution, specifically, complete procurement automation. (In Part II, I’ll illustrate the benefits of eProcurement with a plausible ROI scenario.) Personal productivity devices, such as desktops, laptops, smartphones, and tablet PCs, and the data they generate and retrieve have contributed to a wealth of information and…risks for Long Term Care. If Information Technology (IT) managers are unable to monitor, manage, and protect productivity devices, software distribution, and how information is exchanged and filed, providers run a considerable risk of data loss, non-compliance, and potentially fatally damaging their operations. Implementing sound hardware and data management practices is the responsibility of all providers. IT Asset Management (ITAM) embraces the technology and best practices that can help IT Managers with this critical task.
Personal productivity devices, such as desktops, laptops, smartphones, and tablet PCs, and the data they generate and retrieve have contributed to a wealth of information and…risks for Long Term Care. If Information Technology (IT) managers are unable to monitor, manage, and protect productivity devices, software distribution, and how information is exchanged and filed, providers run a considerable risk of data loss, non-compliance, and potentially fatally damaging their operations. Implementing sound hardware and data management practices is the responsibility of all providers. IT Asset Management (ITAM) embraces the technology and best practices that can help IT Managers with this critical task. Last time, when I addressed the theme of eCommerce evolution, I wrote that for eCommerce to evolve Buyers and Vendors alike must trust each other through communication and consistency in services, processes, and meeting commitments. And they must trust and implement technologies and innovations as well as further refine their practices and reach their goals.
Last time, when I addressed the theme of eCommerce evolution, I wrote that for eCommerce to evolve Buyers and Vendors alike must trust each other through communication and consistency in services, processes, and meeting commitments. And they must trust and implement technologies and innovations as well as further refine their practices and reach their goals.